We recently published a blog about a very new and emerging threat coined “disruptionware,” now faced by workforces in multiple industries – especially focused on workers employed in government and in the health care sector. As first identified and discussed by the Institute for Critical Infrastructure Technology (ICIT), disruptionware is designed to attack the traditional “CIA Triad,” i.e., the confidentiality, integrity and availability of a user’s systems, networks and data. Disruptionware is an emerging form of malware, with a greater adverse impact than more traditional, standalone ransomware attacks, in that it is designed to actually suspend physical operations within a victim organization. Unlike most cyber-attacks focusing on the “IT” networks in a business, disruptionware directly attacks a company’s “Operational Technology” (OT) environments — in short, it attacks a firm’s physical infrastructure in addition to attacking its networks, systems and/or data.
To understand how disruptionware works, one must understand its basic foundational construction. This graphic, reprinted with permission of ICIT, provides an excellent representation of characteristic disruptionware components:
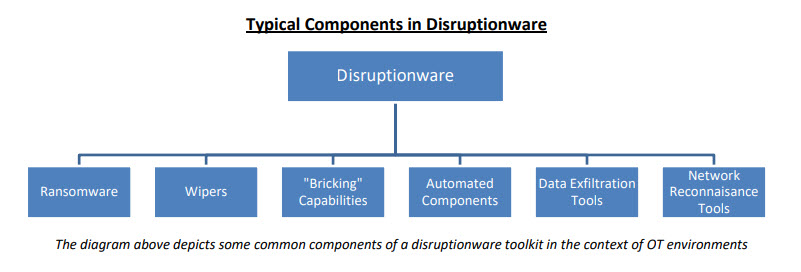
While ransomware is still the leading “go to” form of disruptionware for many cyberattacks, disruptionware introduces many new cyber-attack soldiers to do its bidding, such as:
- Wipers – wiper malware maliciously wipes data making it unrecoverable
- Bricking Capabilities – a PDoS (permanent denial of service attack) malware that renders devices unusable by overwriting portions of the device’s firmware
- Automated Component Attacks – uses tools such as botnets and other automated components to overwhelm a network with inbound traffic, leading to a destructive denial of service attack
- Data Exfiltration Tools – tools used by malicious actors to target, copy and transfer sensitive data from one network to another; causes extreme disruption of employer business focus and severely taxes human resources of the victim company
- Enhanced Network Reconnaissance Tools – tools such as remote access Trojans, key loggers and network-mapping tools that infiltrate and permanently destroy the OT environment of their victims
Many of these tools are designed to do more than just encrypt data in hopes of ransom, but to actually and utterly destroy a user’s systems, networks and data permanently. Due to the ubiquitous and intense nature of these attacks, it is imperative that companies immediately consider, at least to start, hardening their IT and OT networks as much as possible as well as provide social awareness training to their employees to help curtail the spread of disruptionware.
The severe danger of disruptionware attacks on the OT environment of critical infrastructure in places like government institutions and hospitals is that the attacks are tailored to their actual business continuity and physical foundational IT and OT systems. Disruptionware attackers particularly focus on targeting the growing connection (and merging) of IT and industrial control systems (ICS). In doing so, disruptionware is able to heap massive potential damages on organizations that are trying to turn these disparate networks into a single unified system. This threat is highlighted by the huge rise in ransomware attacks alone. According to Cybersecurity Ventures, ransomware attacks are predicted to occur every 11 seconds by 2021, with a cost to victims of over $20 billion, and with global cyber-crime-related damages in 2021 estimated to reach $6 trillion.
There have already been some recently identified disruptionware attacks with losses in the hundreds of millions of dollars, as victim companies were unprepared to defend themselves against the devastating damage caused by these multifaceted attacks. So, the natural next question is why disruptionware is so dangerous despite its lack of advanced “sophistication.” This is because disruptionware:
- Has a high rate of successful compromise
- Requires little to no continued adversarial effort
- Consumes a target’s internal resources very effectively
- Disrupts daily operations
- Has the ability to spread down the supply chain, making it very attractive to cyber-villains, from traditional script-kiddies to nation-state threat actors
Disruptionware was initially very successful in taking advantage of remote desktop protocol (RDP) attacks which, until the last few months, were a reasonably unknown attack point of entry. In July 2019 alone, there were over 805,000 systems considered vulnerable to RDP exploits — making those systems targets for additional attacks in the form of disruptionware.
In short, disruptionware provides another major advantage for cyber-criminals. In many of these attacks, the cyber adversary may still maintain access to the system, thus allowing installation of backdoors, remote-access Trojans or other types of dangerous or unknown malware. ICIT has noted that disruptionware could also stem from cloud-based attacks, due to its ability to maintain “persistent synchronization” and could even potentially attack millions of devices attached by the Internet of Things (IoT). Disruptionware may allow a cyber-criminal to take control of (or destroy) smart appliances in private residences, such as smart washers and dryers or smart thermostats.
With the assistance of outside counsel, organizations are well-advised to begin thinking about how to confront these new forms of cybersecurity threats from both a business and technical perspective. There are, in fact, multiple defenses that can combat these new and emerging disruptionware attacks.
We will discuss those defenses in more depth in my next disruptionware blog.


